What we do
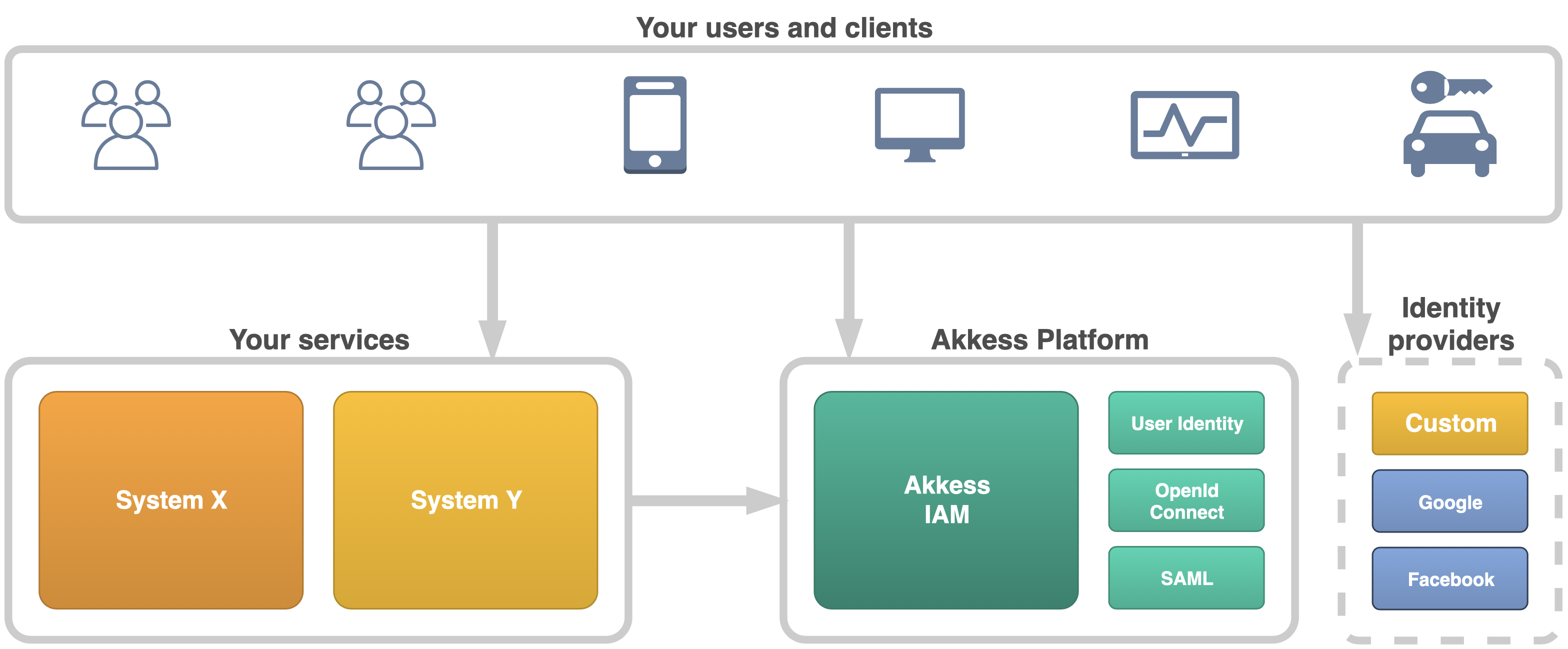
Akkess IAM is a managed service and toolbox to enable secure and reliable access management for any kind of application.
Akkess has all those common features that you can expect from an IAM plus a powerful management console for administration. By integrating with Akkess IAM, you will be able to have the same features as Google and Amazon but with very little effort.
Akkess has developer focus — meaning that it shall be fun to use and complicated things shall be made easy.